When it comes to deploying software, our job as consultants is to ensure reliability, consistency, and security for our clients. Our general approach to addressing these grand tasks is to leverage existing open-source technologies. We recently discovered two open source tools than can help strengthen the security of our Node.js packages on production environments.
Node.js APIs rely heavily on open-source libraries, and the open-source community relies on one another to validate the legitimacy of each individual npm (node packet manager) package. While this open collaboration and policing system works most of the time, sometimes we’ve got to take matters into our own hands. The left-pad incident of 2016 showed us that npm packages don’t always work as intentioned; stressing the importance of individually managing and testing npm libraries. But, at the same time, who really has time to micromanage and audit the sea of dependencies living in their node_modules folder?
The great news is there are tools out there to help raise awareness for npm security issues. Node Security Platform and VulnDB are advisory databases that periodically publish detailed information about known vulnerabilities in Node.js dependencies and guidance on how to fix them.
Another tool, Snyk, offers a command line interface that allows users to audit their dependencies against VulnDB. The Snyk wizard traverses through a user’s node_modules folder & “provides the severity of the issue, a link to a detailed description, the path through which the vulnerable module got into your system…” This command line interface wizard also walks a user through steps for a smooth transition for updating packages.
To run this tool, install snyk & enter the same directory as your node_modules folder and run
npm install –g snyk
snyk wizard
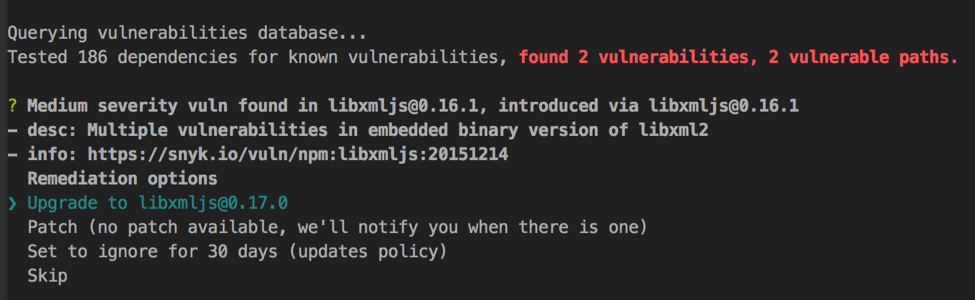

The wizard traverses through npm packages, checks for security issues, ranks the level of risk, and gives the user actionable options. Ignorance is no longer an excuse!
Once a user is comfortable with the patches applied to his/her packages, npm’s shrinkwrap can be used to create a snapshot of all project dependencies and their vulnerability-tested versions.
npm shrinkwrap
Shrinkwrap creates a npm-shrinkwrap.json file that contains a module tree of what’s currently installed in node_modules; thus easing the process of reproducing for production use.
While these two simple tools provide awareness and actionable remediation options, one’s software is only as safe as how often it is checked for new vulnerabilities. Automation is key. Node Security platform and Snyk offer paid servers that continuously monitor subscribed GitHub repositories against their respected databases.
Will running these two tools ensure 100% security regarding node packages? No – but it lays a foundation for creating a system that ensures an effort for increasing security and reliability. We hope that you can incorporate these two very simple, intuitive tools into your product development lifecycle. So far, we’ve found them to be very reliable and of great value.